Presto provides enterprise-grade user authentication mechanisms like LDAP and Kerberos, but a lot of users do not want to go through the complexity of setting up LDAP or Kerberos and would rather have a simpler user authentication mechanism. For such users, Qubole Presto has implemented file-based authentication, where the usernames and passwords are provided to Presto through a file that contains user credentials in a standard format, and users submitting the query are authenticated using this information.
For additional security, the passwords were taken as input in user:password pairs do not support plain text passwords; only hashed passwords are supported. MD5, SHA1, Crypt, and BCrypt hashing algorithms are supported — we recommend using MD5 and BCrypt.
Configuring Filed-Based Authentication
The following configuration needs to be set up in Presto to enable file-based authentication:
- config.properties need to configure FILE as the authentication type and provide the location of the file that contains all valid pairs of the user:password. For example, the following goes into config.properties:
http-server.authentication.type=FILE
authentication.filebased.config-file=/usr/lib/presto/etc/file_auth - The password file, which has pairs of user:password, e.g.:
> cat /usr/lib/presto/etc/file_auth
ankit:$apr1$bCW.IjMe$5/44.P9lNhklw6i54IXoY.
raunaq:{SHA}bWdU2ejuS1lWa0mv11TR2YAoOzs=
sanchit:EY8ULaXsqebTI
punith:$2y$05$/.QHkz9ytxOWwvcE5zMt7O0fabySUNcdKMqVmJpqTOGIRdFfjlSey
In the example below, there are four users:
- ankit: This user’s password is hashed using MD5 and the hashed value is stored as $apr1$bCW.IjMe$5/44.P9lNhklw6i54IXoY.
- raunaq: This user’s password is hashed using the SHA1 algorithm
- sanchit: This user’s password is hashed using the Crypt algorithm
- punith: This user’s password is hashed using the BCrypt algorithm
These configurations can be configured in QDS under Presto Settings on the Edit Cluster page:
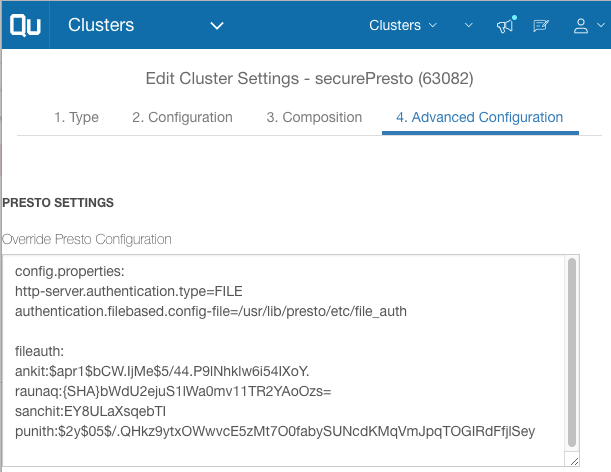
Refer to QDS documentation to understand how to write custom Presto configurations in QDS.
Apart from configuring file-based authentication, Presto should also be configured to use HTTPS, as HTTP is not secure enough to transmit passwords over wire. Hence, Presto clients allow the transmission of passwords only when communicating over HTTPS. Usually, enabling HTTPS requires users to create certificates and configure nodes to use them as mentioned in LDAP documentation. However, QDS users just need to contact [email protected] to enable HTTPS for their clusters, and Qubole takes care of generating certificates, setting up Presto to use them, etc.
Generating a Password File
The password file containing username:password pairs is generated using the standard htpasswd utility, which uses the following syntax:
- Generate MD5 encrypted passwords using `htpasswd -n <UserName>`
- SHA1: Generate SHA1 encrypted passwords using `htpasswd -n -s <UserName>`
- BCrypt: Generate bcrypt-based password using `htpasswd -n -B <UserName>`
- Generate Crypt algorithm-based password using `htpasswd -n -d <UserName>`
Refer to the htpasswd documentation for all the supported options.
While running a Presto client, each user gives their actual password and not the hashed password (e.g. user1 would set username=ankit and password=myPassword). The authentication system will detect that the given password of user1 in the user:password file is MD5 hashed (using the suffix in password), calculate the MD5 hash of the entered password, and compare the two hashes to authenticate user1.
Client Authentication
Users can submit queries to the master node of a Qubole Presto cluster in two ways:
- Via Qubole Data Service (QDS) UI/API/ Qubole ODBC/JDBC Drivers
In this case, there is no impact on users after enabling file-based authentication. QDS takes care of authenticating users and communicating with the Presto Server over HTTPS instead of HTTP. - Via open source clients like JAVA client, Ruby client, JDBC/ODBC Drivers
In this case, QDS middleware is bypassed and the file-based authentication system is used to authenticate the users. Users migrating from contacting an insecure Presto Server to a Presto Server using the File-Based Authentication system need to take care of the following changes:- Presto Server will now be accessible over HTTPS and on port 8443.
- Username and passwords are mandatory
For example, the JDBC URL to contact insecure Presto Server changes from jdbc:presto://example.net:8080/hive/sales to jdbc:presto://example.net:8443/hive/sales?user=test&password=secret&SSL=true
A file-based authentication system provides a simpler way to authenticate users in Presto without extensive investment in hosting LDAP or Kerberos services. Qubole released file-based authentication as a Beta feature in June 2018, and it was released for GA use in September 2018 with QDS Presto versions 0.180 and above supporting it.
If you want to try out this feature in Qubole Presto, set up your cluster with the configuration mentioned in this blog, and reach out to [email protected] to enable HTTPS on your cluster, then you should be good to go.



